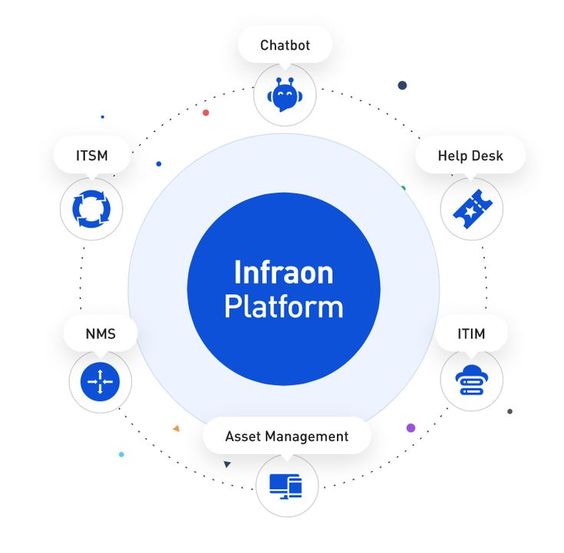
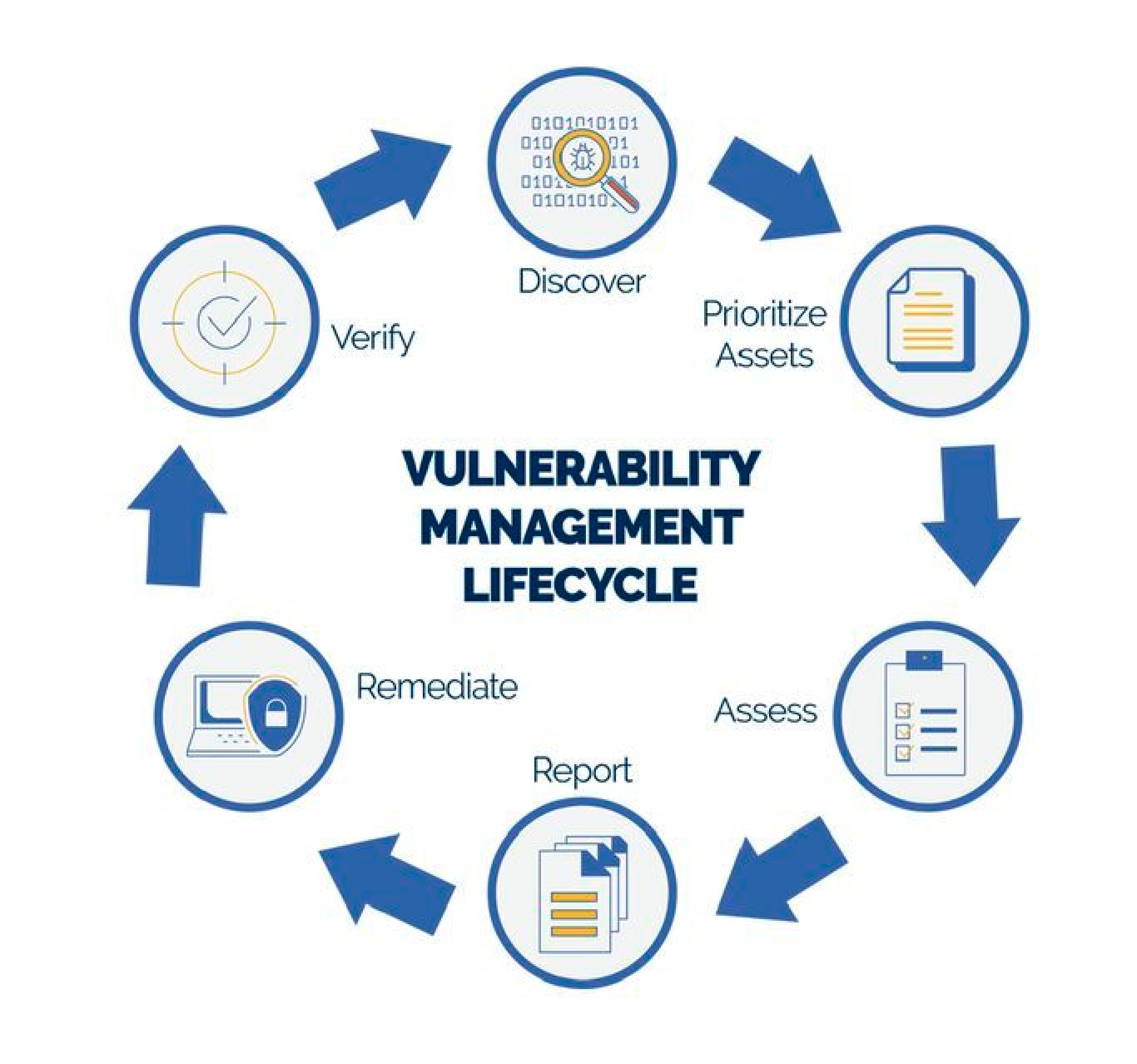
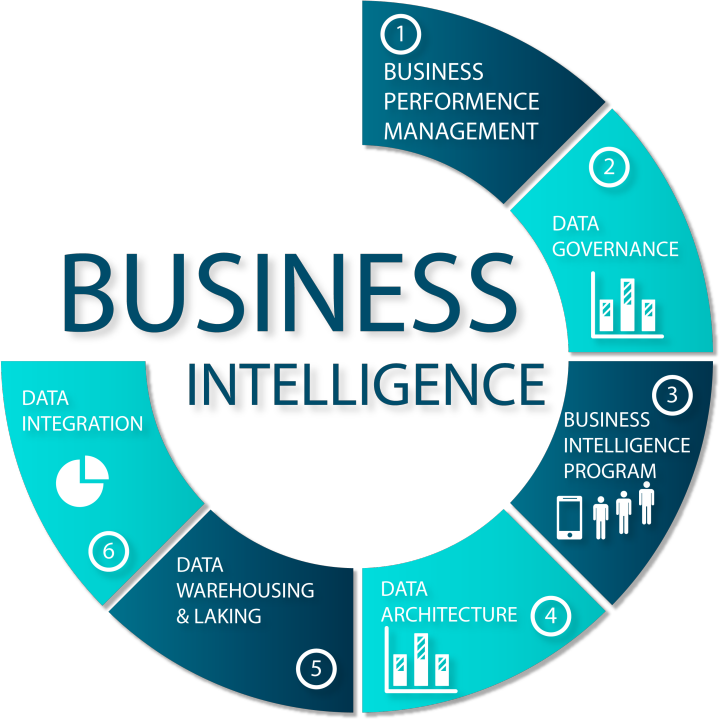
Mobile app development & AI
Introduction The intersection of mobile app development and artificial intelligence (AI) is a thriving area of technology, offering a range of innovative solutions and enhancements for mobile experiences. Here are some key ways AI is being integrated into mobile app