Introduction
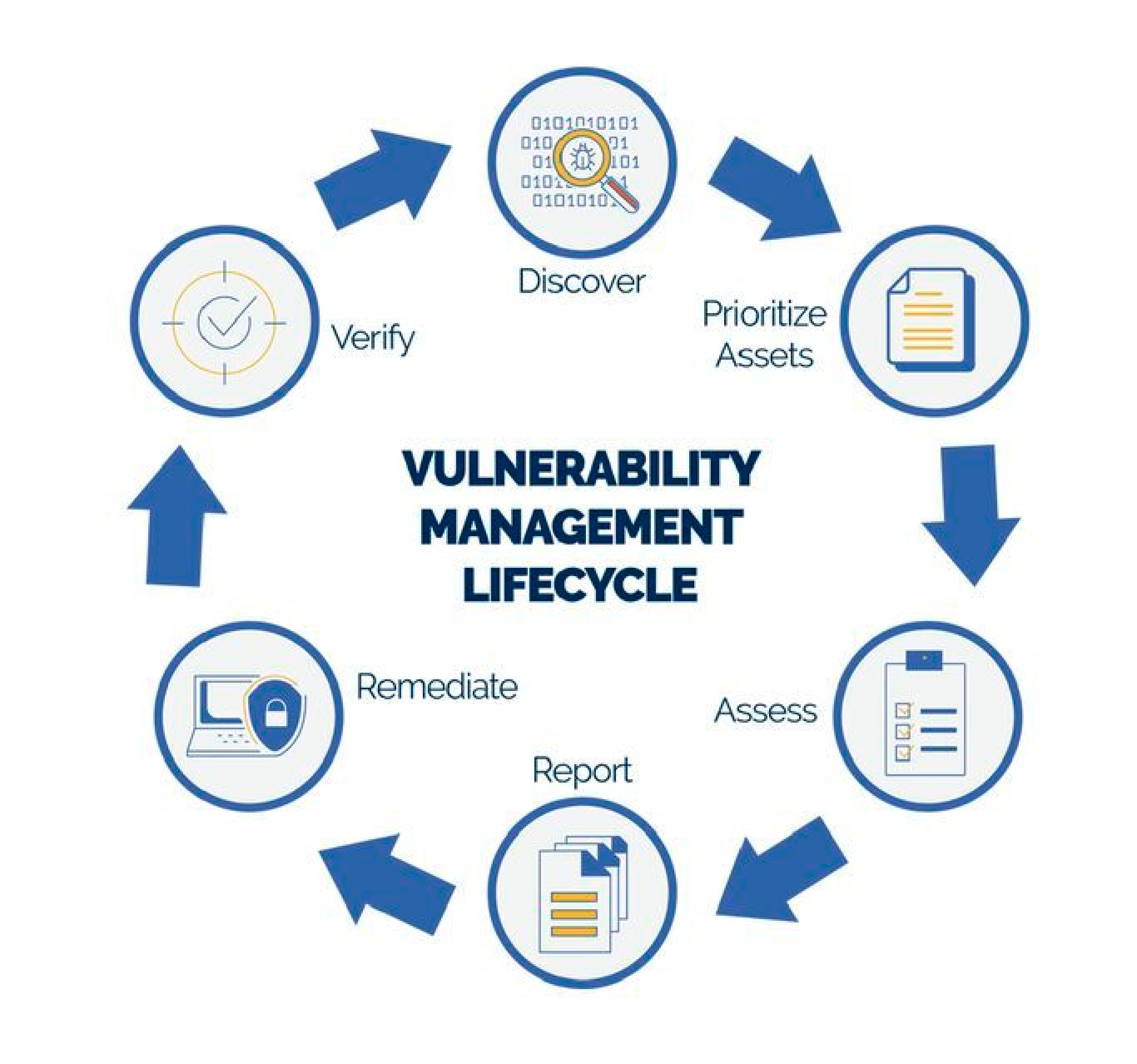
Vulnerability management is a comprehensive approach to identifying, assessing, prioritizing, mitigating, and monitoring security vulnerabilities in an organization’s information technology infrastructure. It is a fundamental component of cybersecurity and is essential for maintaining the security and integrity of systems, networks, and data. Here’s a breakdown of the key aspects of vulnerability management:
1.Identification: The first step in vulnerability management is to identify potential vulnerabilities in your IT environment. This can be done through various means, including automated vulnerability scanning, manual testing, and monitoring of security advisories.
2.Assessment: Once vulnerabilities are identified, they need to be assessed to determine their severity and potential impact. This assessment often involves assigning a risk level or score to each vulnerability. Common methods for assessment include the Common Vulnerability Scoring System (CVSS) and other risk assessment frameworks.
3.Prioritization: Not all vulnerabilities are of equal importance. Prioritization involves ranking vulnerabilities based on their severity, potential impact on the organization, and other contextual factors. This helps security teams focus their efforts on addressing the most critical issues first.
4.Verification: It’s crucial to confirm that the mitigation measures were effective. This often involves re-testing the systems to ensure that the vulnerabilities have been addressed. Verification helps in preventing false positives and ensuring that the organization is no longer exposed to the identified risks.
5.Reporting and Documentation: Comprehensive documentation and reporting are essential for compliance, auditing, and accountability. Reports should include details on identified vulnerabilities, their status, and actions taken to mitigate them.
Different types of Security Vulnerabilities:

1.Unpatched Software
Unpatched security vulnerabilities allow attackers to run a malicious code by leveraging a known security bug that has not been patched. The adversary will try to probe your environment looking for unpatched systems, and then attack them directly or indirectly.
2.Misconfiguration
System misconfigurations (e.g. assets running unnecessary services, or with vulnerable settings such as unchanged defaults) can be exploited by attackers to breach your network. The adversary will try to probe your environment looking for systems that can be compromised due to some misconfiguration, and then attack them directly or indirectly.
3.Weak Credentials
An attacker may use dictionary or brute force attacks to attempt to guess weak passwords, which can then be used to gain access to systems in your network.
4. E-commerce apps
If you have bought anything online, you must be acquainted with one of the most usual web applications, and that is eCommerce.
If a web app is in the form of a shop or store, this kind of development is categorized as eCommerce.